Terms
  |
Internet of Things Privacy
The special considerations required to protect the information of individuals from exposure in the IoT environment, where almost any physical or logical entity or object can be given a unique identifier and the ability to communicate autonomously over the Internet or similar network. |
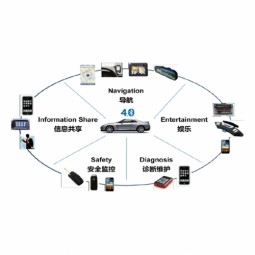  |
Internet of Vehicles
Internet of Vehicles (IoV) technology refers to dynamic mobile communication systems that communicate between vehicles and public networks using V2V (vehicle-to-vehicle), V2R (vehicle-to-road), V2H (vehicle-to-human) and V2S (vehicle-to-sensor) interactions. |
  |
Internet Protocol Version 6
Internet Protocol Version 6 (IPv6) is also called IPng (Internet Protocol next generation), and it is the newest version of the Internet Protocol (IP) reviewed in the IETF standards committees to replace the current version of IPv4 (Internet Protocol Version 4). |
  |
Internet Protocol Version 4
Internet Protocol version 4 (IPv4) is the fourth version of the Internet Protocol (IP). IPv4 is a connectionless protocol for use on packet-switched networks. It operates on a best effort delivery model, |
  |
Interoperability
Interoperability is the ability of a system or a product to work with other systems or products without special effort on the part of the customer. It becomes a quality of increasing importance for information technology products as the concept that "The network is the computer" becomes a reality. |
  |
IoT Botnet
An IoT botnet is a group of hacked computers, smart appliances, and Internet-connected devices that have been co-opted for illicit purposes. An IoT botnet is larger in scale, with hundreds of thousands of compromised devices. |
  |
IoT Security
IoT security is the area of endeavor concerned with safeguarding connected devices and networks in the Internet of things. IoT involves adding internet connectivity to a system of interrelated computing devices, mechanical and digital machines, objects, animals, and/or people. |
  |
IPv6 Address
A 128-bit alphanumeric string that identifies an endpoint device in the Internet Protocol Version 6 (IPv6) addressing scheme. IPv6 addresses are classified by the primary addressing and routing methodologies common in networking: unicast addressing, anycast addressing, and multicast addressing. |
  |
IPv6 over Low -Power Wireless Personal Area Networks
IPv6 over Low -Power Wireless Personal Area Networks (6LoWPAN) is the name of a concluded working group in the Internet area of the IETF (Internet Engineering Task Force). |
|
IT-OT Convergence
IT-OT Convergence is a process of integrating information technology (IT) systems. It is used for data-centric computing with operational technology (OT) systems to monitor events, processes, and devices and make adjustments in enterprise and industrial operations. |
|
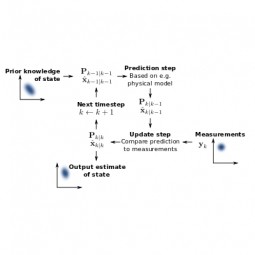  |
Kalman Filter
An algorithm that produces estimates of the state of a system based on a sequence of noisy observations, making it an important topic in control systems. |
|
Kubernetes
Kubernetes is a portable and open-source platform for managing containerized workloads and applications that facilitates both declarative configuration and automation. |
|
  |
Least Privilege
The principle that a security architecture should be designed so that each entity is granted the minimum system resources and authorizations that the entity needs to perform its function. |
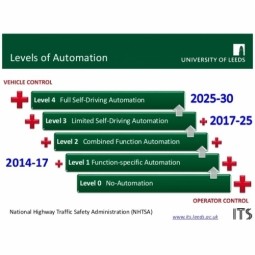  |
Level 0 Automated Vehicle
The "no-automation" baseline of the 5-level NHTSA vehicle classification system. The driver is under the complete and sole control of the primary vehicle controls - brake, steering, throttle, and motive power - at all times. |
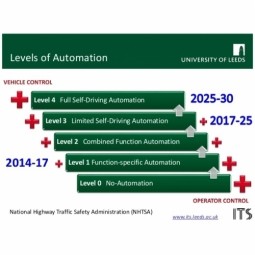  |
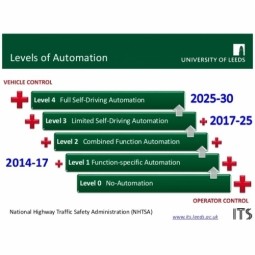
Level 3 Automated Vehicle
Limited Self-Driving Automation is the fourth level of the 5-level NHTSA vehicle classification system. Vehicles at this level of automation enable the driver to cede full control of all safety-critical functions under certain traffic or environmental conditions. |
  |
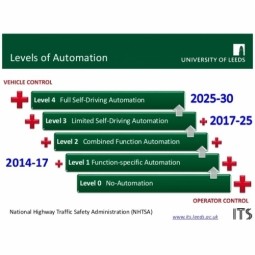
Level 4 Automated Vehicle
Full Self-Driving Automation is the fifth and highest level of the 5-level NHTSA vehicle classification system. The vehicle is designed to perform all safety-critical driving functions and monitor roadway conditions for an entire trip. |
  |
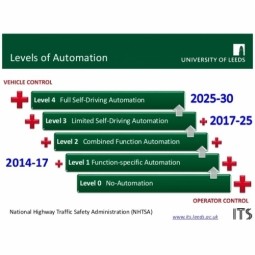
Level 1 Automated Vehicle
Function-specific Automation is the second level of the 5-level NHTSA vehicle classification system. Automation at this level involves one or more specific control functions. |
  |
Level 2 Automated Vehicle
Combined Function Automation is the third level of the 5-level NHTSA vehicle classification system. This level involves automation of at least two primary control functions designed to work in unison to relieve the driver of control of those functions. |
 |
Light Field
Light Field refers to an optical technology employed by companies to enable objects to be displayed at varying focal planes, allowing for the illusion of depth in an augmented reality experience. |
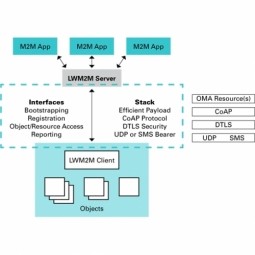  |
Lightweight M2M
Lightweight M2M (LWM2M) enabler defines the application layer communication protocol between an LWM2M Server and an LWM2M Client, which is located in an LWM2M Device. The OMA Lightweight M2M enabler includes device management and service enablement for LWM2M Devices. |
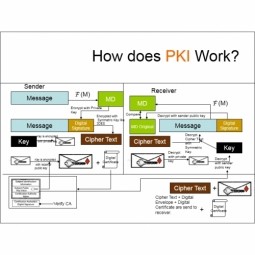  |
Lightweight Public Key Infrastructures (PKI)
A public key infrastructure (PKI) supports the distribution and identification of public encryption keys, enabling users and computers to both securely exchange data over networks such as the Internet and verify the identity of the other party. |
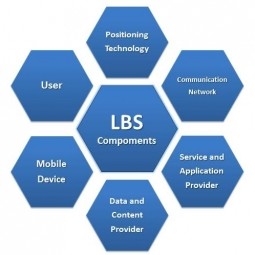  |
Location Based Service
Location based services (LBS) are services offered through a mobile phone and take into account the device’s geographical location. LBS typically provide information or entertainment. |
  |
Location Privacy
A technique used in location-based services or information systems to protect the location of the users by slightly altering or generalizing their location. |
  |
Long Term Evolution
Long Term Evolution (LTE) is a standard for 4G wireless broadband technology that offers increased network capacity and speed to mobile device users. |
  |
LoRaWAN
Standardized by the LoRa Alliance, the LoRaWAN specification allows low bit rate communication between connected objects in a wide area network (WAN). |
  |
Low Power and Lossy Networks
Low Power and Lossy Networks (LLNs) are comprised of embedded devices with limited power, memory, and processing resources. LLNs are typically optimized for energy efficiency, may use IEEE 802.15.4. |
  |
Low-Power, Wide-Area Network
Low-Power, Wide-Area Network (LPWAN) is built specifically for M2M communications and offers long-range, low-power consumption. They solve cost and battery-life issues that cellular technology cannot, and LPWA networks solve range issues that technologies like Bluetooth or BLE struggle with. |
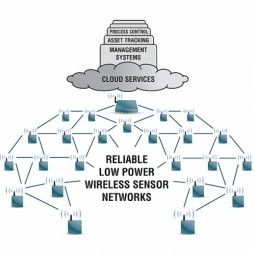  |
Low Power Wireless Sensor Network
A group of spatially distributed, independent devices that collect data by measuring physical or environmental conditions with minimal power consumption. |
  |
LTE-Unlicensed
LTE-Unlicensed (LTE-U) is a proposal, originally developed by Qualcomm, for the use of the 4G LTE radio communications technology in unlicensed spectrum. It would serve as an alternative to carrier-owned Wi-Fi hotspots. |
_6.jpg) |
LTE-Vehicular
LTE-Vehicular (LTE-V) is the application of vehicular connectivity over the existing operator mobile network infrastructure. LTE-V can be rapidly and inexpensively deployed by reusing the existing cellular infrastructure and spectrum. |
